Microsoft has announced a set of critical Remote Desktop Protocol (RDP) security vulnerabilities. RDP on Microsoft Server 2008/2012, Windows 7 and newer versions of Windows are affected.
An unauthenticated attacker can exploit this vulnerability by connecting to the target system using the Remote Desktop Protocol (RDP) and sending specially crafted requests. This vulnerability is pre-authentication and requires no user interaction.
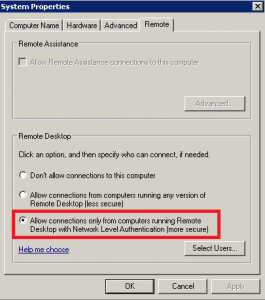
The RDP NLA (network level authentication) security setting mitigates this vulnerability from unauthenticated external attackers and it is the default for our Windows VPS. However, some clients may have disabled NLA.
The RDP NLA security setting can be found by going to the following location in Windows.
Control Panel > System > Remote settings > allow remote connections to this computer > [check] allow connections only from computers running Remote Desktop with Network Level Authentication (recommended)
All Windows VPS clients are recommended to update their VPS as soon as possible as well as double check to ensure the RDP NLA higher security setting is enabled.
Windows 2008/2012 VPS can be updated by going to “Start > Control Panel > Windows Update”.
Windows 2016/2019 VPS can be updated by going to “Start > Settings > Update & Security”.
References:
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2019-1181
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2019-1182
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2019-1222
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2019-1226
https://msrc-blog.microsoft.com/2019/08/13/patch-new-wormable-vulnerabilities-in-remote-desktop-services-cve-2019-1181-1182/